Part 2 : Cryptography - The Hybrid Encryption
Techniques of cryptography used in an enterprise application.
Let's dive into this article to see how we can put cryptography into action. We'll look at encryption, decryption, signing, verification, and other operations to get a clearer picture.
If you haven't checked out my article on introduction to cryptography. Consider reading it as it gives you a basic overview of cryptography.
Which type of encryption technique is suitable for an enterprise application and why?
we know that symmetric encryption uses a single key for encrypting and decrypting the data, and not so complex mathematical operations which contributes in faster processing speeds of transforming the data.
Where as asymmetric encryption is slower because of it's computational complexity which involves more rounds of processing of data transformation, it also uses long key lengths for a greater security.
considering the above two types of encryption techniques, as asymmetric is strong in security and slower in processing and symmetric is faster but not secure when compared to asymmetric, which encryption mechanism should be used in an enterprise application where high performance and strong security implementation matters?
Hybrid Encryption
So, this solves the problem. Hybrid encryption is a mechanism of using both symmetric and asymmetric encryption techniques.
Let us explore how it is acheived :
Note that, in symmetric encryption we are using a key that encrypts the data and same key is used to decrypt the data too. Here, in hybrid encryption process, we use Encrypt Key Encrypt Message (EMEK) mechanism.
Let us try to solve bob's problem using hybrid encryption.
Problem : Bob wants to send alice some data through a secure medium, bob needs to ensure that data is encrypted before it reaches to alice. Using symmetric cryptography bob could not perform a secure encryption, using asymmetric technique his application performance lags.
Solution :
Keys to perform operations: we need one symmetric key (bob's), one asymmetric public key(Alice's).
Process of encryption : so, here instead of encrypting the data directly we are actually using the asymmetric encryption to encrypt the bob's symmetric key with alice's public key. confused ? let's see the below figure:
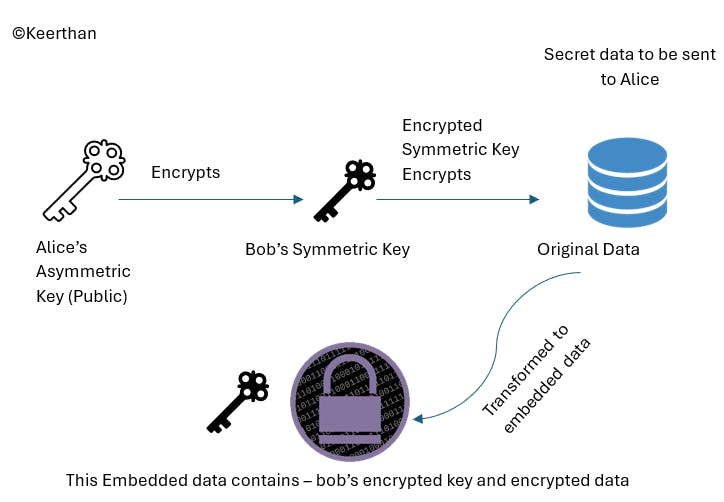
Note: Here, the public key being used is the alice's, why? because, the private key and public key are actually a pair. If a public key encrypts the data, the one and only matching private key decrypts it. So, If bob wants to send the data to alice, the alice's public key should be used to encrypt the data so that only alice can decrypt it with her own private key. Let us actually go through this in my further articles of how key management works.
Process of decryption : At the alice's end, she will initially decrypt the bob's shared symmetric key and then that key is used to decrypt the original data.
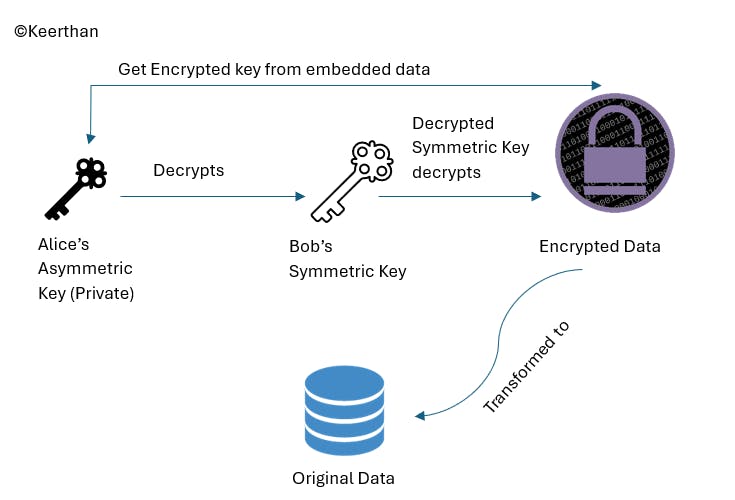
- Conclusion : This is how hybrid encryption technique is performed which supports both performance and robust security suitable for an enterprise application.
Cryptography series continues, In our next blog, Let us explore about the concepts of the public key infrastructure, the certificate/key management and let us create cryptographic keys using openssl.
Until then, consider to follow me for such content.
Thanks for reading :-D
Regards,
Sai Keerthan,
Junior Developer.
